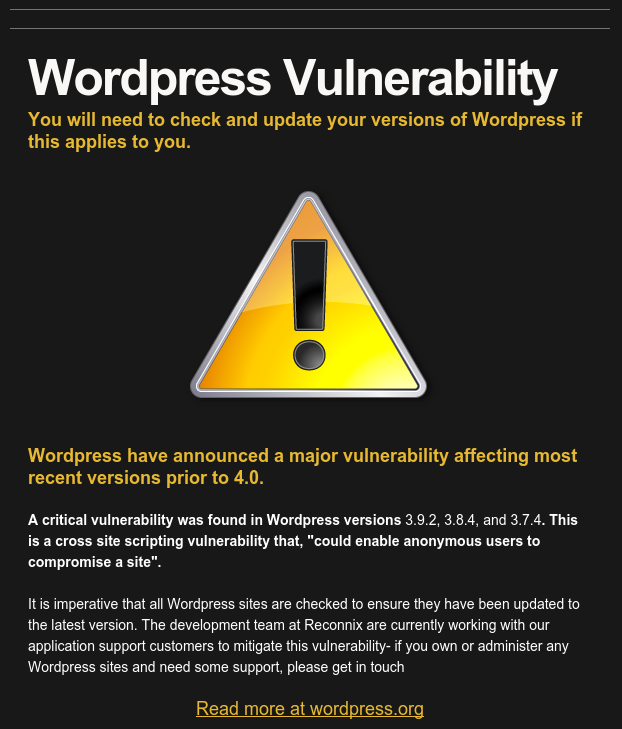
Late yesterday afternoon (24/11/14), Reconnix became aware of a vulnerability within WordPress. The problem is with a cross-site scripting vulnerability that affects versions 3.9.2 and earlier. This particular vulnerability could allow an attacker to enter code on to the comments section of a blog post, enabling them to take control of the administrator’s account.
So, as with all security alerts, we generated and released a newsletter via MailChimp, alerting all our clients of this vulnerability. However, we had some new clients that had not yet gone through MailChimp’s opt-in procedure to be on our mailing list. So, in order for them to see our alert, we sent them a link via MailChimp’s social share option.
However, this is where we spotted a problem. When we shared the link for the alert, we noticed that the snippet generated gave information to another alert that we raised on the 8th August 2014. Below are a series of screenshots that show our particular dilemma.
- 1. This is the alert newsletter that we generated yesterday (24/11/14) on MailChimp:
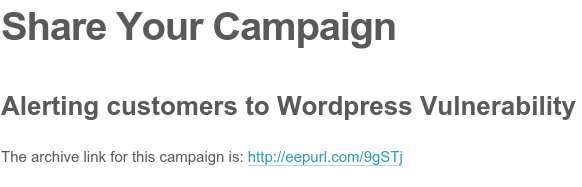
2. This is a screenshot from MailChimp’s social share page. The page generates a link to the campaign that you want to share. In this image, you can see the link that MailChimp generated (http://eepurl.com/9gSTj) for the WordPress Vulnerability alert that we created yesterday (24/11/14):
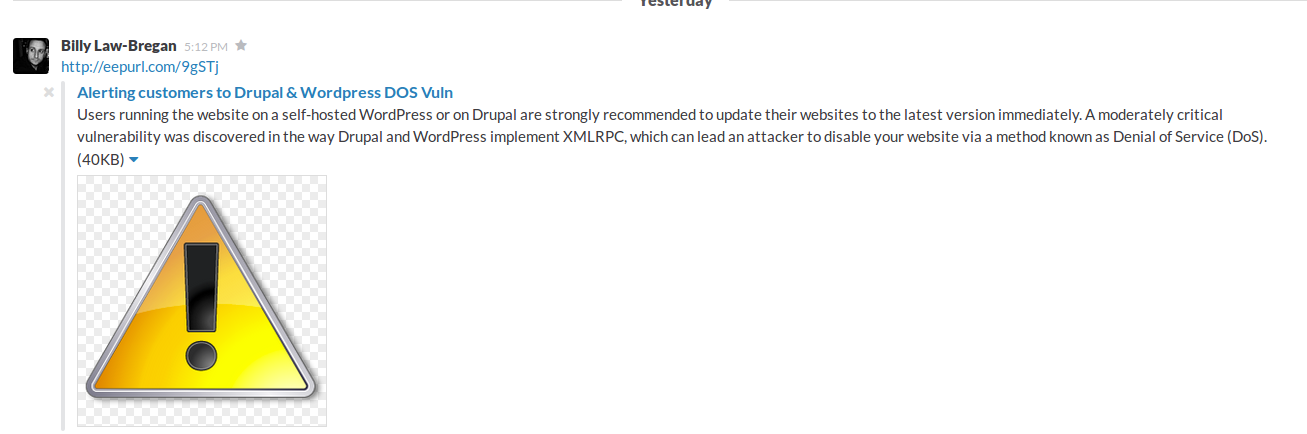
3. However, when we pasted the link (http://eepurl.com/9gSTj) into a social media site, the snippet generated was that of a previous Drupal and WordPress vulnerability alert:
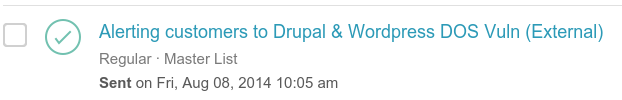
4. This is the alert to which the snippet is referring. Notice that the date of this particular release was 8th August 2014:
Interestingly, when you clicked on the link that MailChimp generated, it took you to the correct landing page.
So what? Well, from our point-of-view, this could be a potential problem. If our clients saw the link and the generated snippet, they may assume that they have already received this information and miss out on vital security information. Not only could this pose a potential security risk for our clients, it could also lead to our customers losing confidence in our services. We need to get this monkey off our backs.
Contact Us
